Reykjavik - CTFLearn
Reykjavik
DESCRIPTION : Good beginning Reversing challenge - jump into gdb and start looking for the flag!
Basic Info
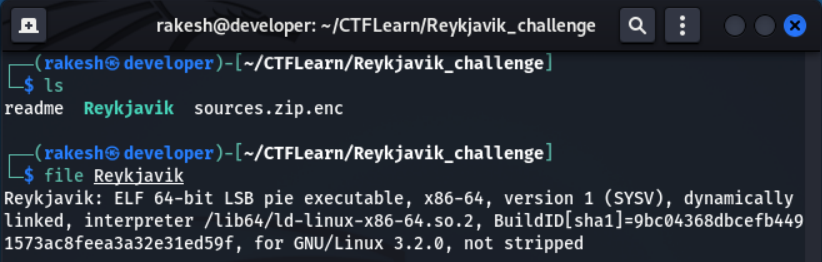
File command
It is 64 Bit elf LSB binary
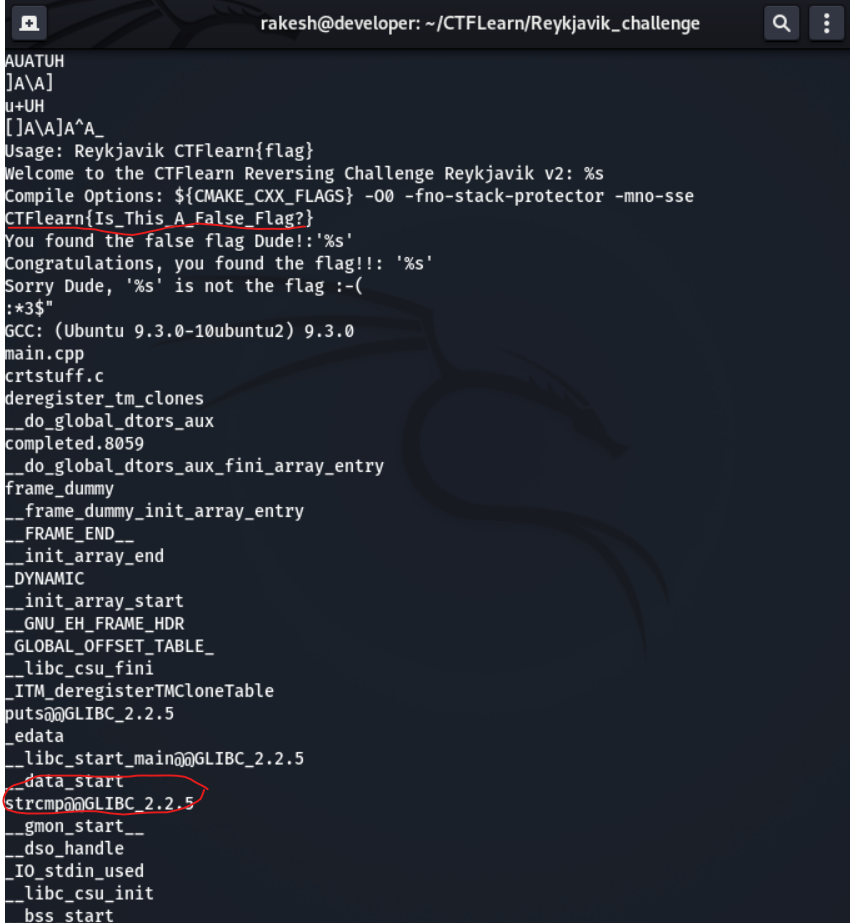
Strings comma
There is some interesting strings.
- CTFLearn{Is_This_A_False_Flag?}
- strcmp@GLIBC
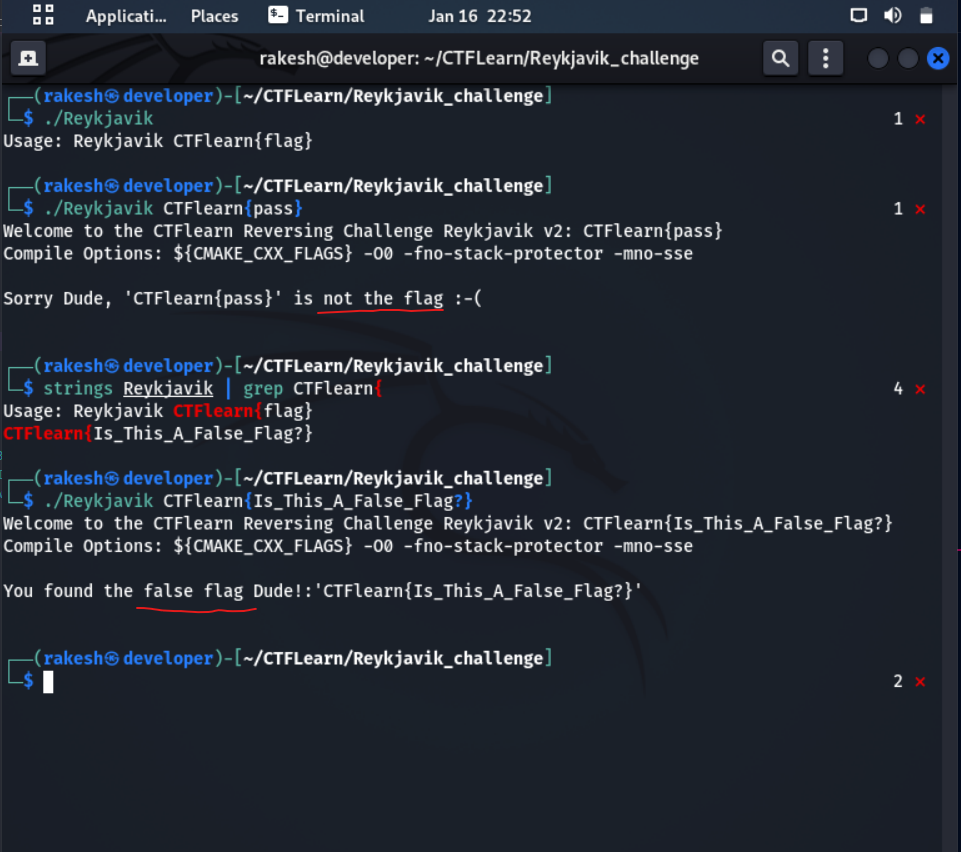
Run the binary
- It want some system argument, In the format of ./Reykjavik CTFLearn{flag}
- Let's try the binary with this argument ( CTFLearn{pass} )
- Then output is "Sorry Dude, '(input)' is not the flag :-(
- Try another time, but this time run the binary with this argument ( CTFLearn{Is_This_A_False_Flag?} )
- The Output is this is false flag Dude.
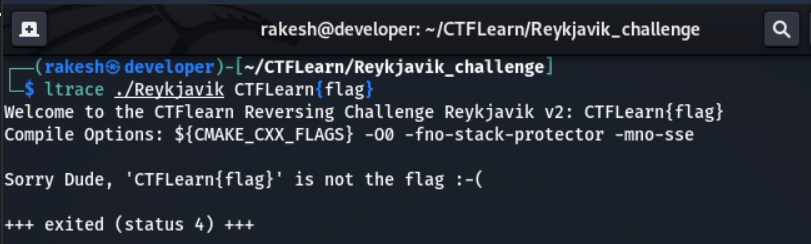
- Let's analysis the binary with ltrace command, because this binary has a strcmp library call.
Ltrace commnad
- It doesn't show any library call.
- Let's analysis the binary in gdb.
GDB
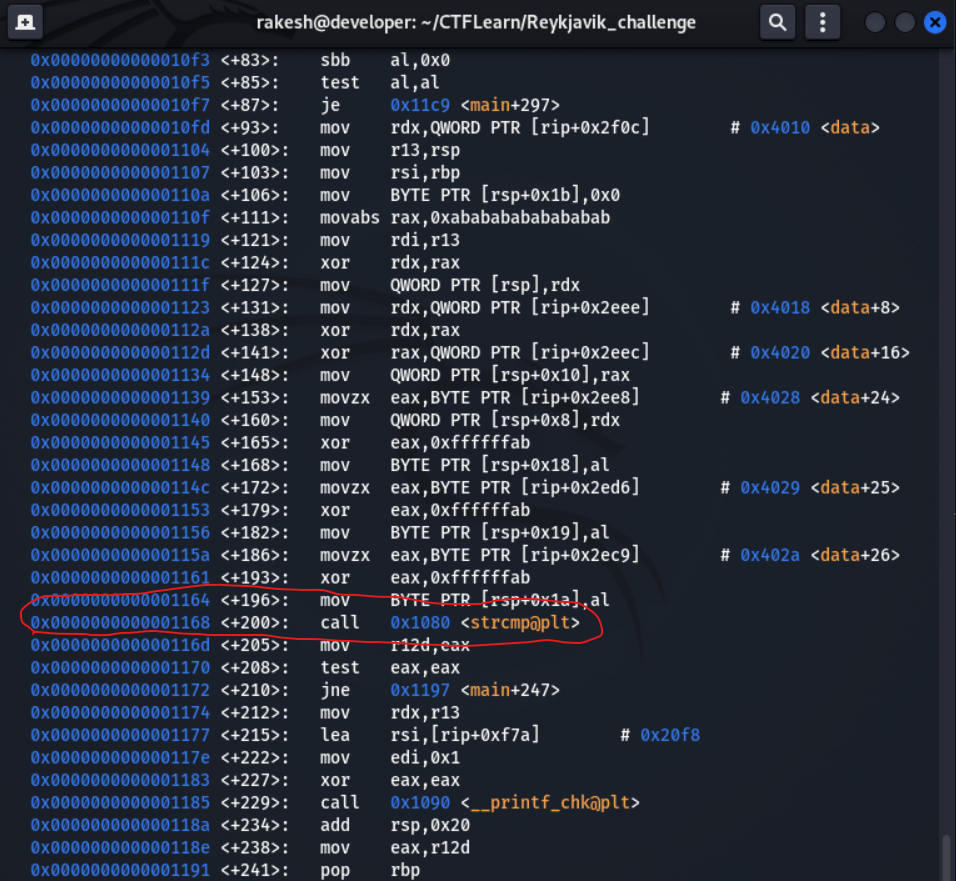
- Disassemble the main function.
- I quick found the strcmp instruction.
- Let's set the breakpoint in strcmp instruction.
- Run the binary with CTFLearn{flag} as argument.
- It compare two string, the s1 has the CTFlearn{Eye_l0ve_Iceland_} and the s2 has the value of our input. (flag)
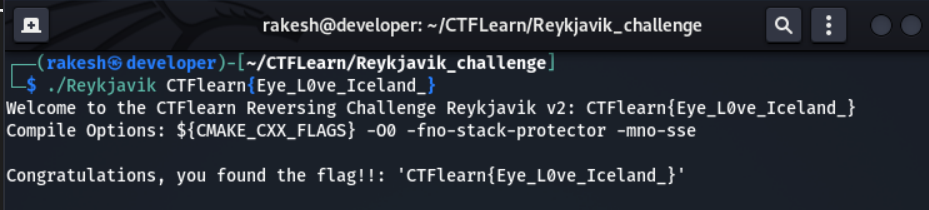
Run the binary
Check the value of s1 is flag or not.
The Output is Congrulation, you found the flag.
The flag is CTFlearn{Eye_L0v3_Iceland_}